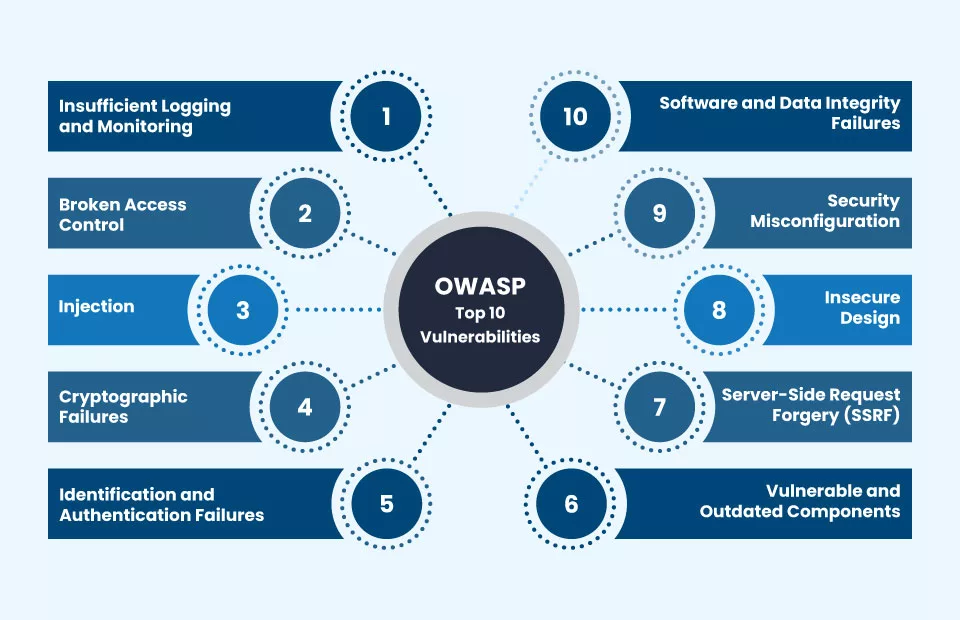
The OWASP Top 10 is a globally recognized standard for identifying the most critical web application security risks. It is a valuable resource for developers, security professionals, and organizations striving to protect their applications from common vulnerabilities. While the OWASP Top 10 is universal, its impact and relevance can vary by region. In Brazil, the digital landscape has been rapidly evolving, and so have the security challenges. In this article, we will explore the OWASP Top 10 in the context of Brazil and discuss how these vulnerabilities manifest in the Brazilian cybersecurity environment.
What is the OWASP Top 10?
The OWASP Top 10 is a list compiled by the Open Web Application Security Project (OWASP), an online community dedicated to improving web application security. This list identifies and categorizes the most common and critical security risks in web applications. It serves as a guide to help organizations prioritize security measures to mitigate potential attacks.
The OWASP Top 10 is updated periodically to reflect the ever-changing nature of the web application landscape, including the new threats posed by evolving technology. By addressing these risks, organizations can significantly reduce the chances of security breaches and data leaks.
OWASP Top 10 2021: What’s New for Brazil?
The OWASP Top 10 list gets updated every few years, with the latest edition being the 2021 update. While the general trends in cybersecurity have remained consistent, certain vulnerabilities are more prominent in specific regions. Brazil, with its growing digital economy, faces a unique set of challenges. Below, we will discuss the updated OWASP Top 10 and the risks they pose to Brazilian organizations.
1. Broken Access Control
Broken access control refers to flaws that allow attackers to bypass restrictions and gain unauthorized access to data or functionality. In Brazil, many organizations struggle with ensuring proper access control, particularly in legacy systems or poorly managed web applications. This risk is amplified in industries like e-commerce and financial services, where sensitive data is frequently processed.
Common Examples:
- Users being able to access resources or data from other users without permission.
- Insufficient role-based access control (RBAC), enabling unauthorized users to perform actions they shouldn’t.
2. Cryptographic Failures
Cryptography is a crucial part of protecting sensitive data, yet many Brazilian companies fail to implement it properly. Whether it’s weak encryption algorithms or improper storage of keys, this vulnerability remains a significant issue. Brazil, with its increasing number of data privacy laws and regulations, such as the LGPD (Lei Geral de Proteção de Dados), must prioritize securing data both in transit and at rest.
Common Examples:
- Storing sensitive information, such as passwords, in plain text or with weak encryption.
- Using outdated or weak cryptographic algorithms.
3. Injection Attacks
Injection flaws, such as SQL injection, are among the oldest and most well-known vulnerabilities in web applications. These attacks occur when untrusted data is sent to an interpreter as part of a command or query. In Brazil, many organizations still rely on legacy code and outdated frameworks, leaving them vulnerable to injection attacks.
Common Examples:
- SQL injection attacks leading to unauthorized database access.
- Command injection vulnerabilities enabling attackers to execute malicious commands.
4. Insecure Design
Insecure design flaws are vulnerabilities that arise from poor architectural decisions and design choices. Brazil’s rapidly digitizing economy has led to many fast-paced deployments without considering security implications. These poor design choices can lead to a significant increase in security risks.
Common Examples:
- Applications that lack proper authentication mechanisms.
- Insufficient validation and sanitization of input, leaving the application vulnerable to various attacks.
5. Security Misconfiguration
Security misconfigurations occur when applications or servers are set up incorrectly, leaving them open to attack. Many organizations in Brazil are still using default configurations in web servers or not following best practices for securing their applications.
Common Examples:
- Leaving unnecessary services enabled, such as debug modes, on production servers.
- Failing to update software with the latest security patches.
6. Vulnerable and Outdated Components
Many Brazilian companies use open-source components or third-party software in their applications. However, not keeping these components up to date with security patches can lead to vulnerabilities. Attackers often target known flaws in outdated libraries and frameworks.
Common Examples:
- Using outdated libraries that are known to have security flaws.
- Failure to monitor for vulnerabilities in third-party components.
7. Identification and Authentication Failures
Weaknesses in identification and authentication mechanisms are common vulnerabilities in many Brazilian organizations. Poor password policies, insecure session management, and improper user authentication all contribute to this category of risks. Brazil’s digital banking and e-commerce industries, in particular, must take extra care in securing user identities.
Common Examples:
- Insufficient password policies, such as allowing weak or easily guessable passwords.
- Failing to invalidate sessions properly after users log out.
8. Software and Data Integrity Failures
Software and data integrity failures occur when applications fail to properly protect data from unauthorized modification. For Brazilian organizations handling sensitive financial data or customer information, ensuring the integrity of their software and data is paramount.
Common Examples:
- Failure to validate code or software updates before deployment.
- Insufficient protection against unauthorized changes to application code.
9. Security Logging and Monitoring Failures
Effective security logging and monitoring are essential for detecting and responding to attacks. In Brazil, many organizations fail to implement adequate logging practices, making it difficult to track suspicious activity and respond to incidents quickly.
Common Examples:
- Lack of centralized logging for application and system logs.
- Failure to monitor logs for signs of suspicious activity, such as failed login attempts.
10. Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) occurs when an attacker tricks a server into making requests to internal systems or external services that are not intended for public access. SSRF vulnerabilities are often found in applications that interact with external APIs or internal services.
Common Examples:
- An attacker using SSRF to access internal services behind a firewall.
- Misconfigured cloud infrastructure exposing sensitive internal resources.
How to Protect Against OWASP Top 10 Risks in Brazil?
Brazilian organizations can take several steps to mitigate the risks highlighted in the OWASP Top 10. These include:
- Regular Security Audits: Conducting routine security assessments and code reviews to identify and fix vulnerabilities.
- Adopting Secure Development Practices: Incorporating security into the development lifecycle, such as using secure coding techniques and adopting threat modeling.
- Employee Training: Educating employees and developers about security best practices to reduce human errors that can lead to security breaches.
- Patch Management: Keeping software and third-party components up to date with the latest security patches.
- Use of Security Tools: Employing automated security testing tools to identify vulnerabilities in applications and infrastructure.
FAQs
Q: Why is the OWASP Top 10 important for Brazilian organizations?
The OWASP Top 10 helps Brazilian organizations identify and address the most critical web application security risks, reducing the chances of data breaches and ensuring compliance with privacy regulations like LGPD.
Q: How can I ensure that my organization is following the OWASP Top 10 guidelines?
You can implement secure coding practices, conduct regular security audits, and use automated security tools to continuously monitor your applications for vulnerabilities.
Q: Are injection attacks still a major risk in Brazil?
Yes, injection attacks remain a significant threat, particularly in older systems and applications that haven’t been updated with modern security measures.
Conclusion
The OWASP Top 10 remains an essential guide to securing web applications, and its relevance is particularly critical for Brazilian organizations in today’s rapidly evolving digital landscape. By addressing these risks, companies can build more secure applications and protect sensitive data from cyber threats. As the digital economy continues to grow in Brazil, following OWASP Top 10 best practices will be crucial to ensuring that applications remain secure and resilient in the face of emerging challenges.